Teamapp File Type Not Accepted
This browser is no longer supported.
Upgrade to Microsoft Edge to have reward of the latest features, security updates, and technical support.
Manage app permission policies in Microsoft Teams
Every bit an admin, you can use app permission policies to control what apps are available to Microsoft Teams users in your arrangement. You can allow or block all apps or specific apps published by Microsoft, tertiary-parties, and your arrangement. When you block an app, users who have the policy are unable to install information technology from the Teams app store. You must be a global admin or Teams service admin to manage these policies.
Yous manage app permission policies in the Microsoft Teams admin center. You can use the global (Org-wide default) policy or create and assign custom policies. Users in your organisation will automatically get the global policy unless you lot create and assign a custom policy. After you edit or assign a policy, it tin can take a few hours for changes to take effect.
Note
Org-broad app settings override the global policy and any custom policies that you create and assign to users.
If your organization is already on Teams, the app settings yous configured in Tenant-broad settings in the Microsoft 365 admin middle are reflected in org-wide app settings on the Manage apps folio. If you're new to Teams and simply getting started, by default, all apps are allowed in the global policy. This includes apps published by Microsoft, third-parties, and your organization.
Say, for case, y'all want to block all third-party apps and let specific apps from Microsoft for the HR team in your organization. Kickoff, yous would go to the Manage apps page and make sure that the apps that y'all desire to allow for the HR team are allowed at the org level. And so, create a custom policy named HR App Permission Policy, set it to block and let the apps that you want, and assign it to users on the HR squad.
Note
If you deployed Teams in a Microsoft 365 Authorities Customs Cloud High (GCCH) and Department of Defense force (DoD) environment, see Manage org-broad app settings for Microsoft 365 Government to larn more about third-party app settings that are unique to GCCH and DoD.
Create a custom app permission policy
If yous want to control the apps that are available for different groups of users in your organization, create and assign one or more custom app permission policies. Yous can create and assign dissever custom policies based on whether apps are published by Microsoft, third-parties, or your organization. It'southward of import to know that after yous create a custom policy, you tin't change it if third-party apps are disabled in org-wide app settings.
-
Log in to Teams admin center
-
In the left console, go to Teams apps > Permission policies.
-
Select Add.
-
Enter a name and description for the policy.
-
Under Microsoft apps, 3rd-political party apps, and Custom apps, select one of the post-obit:
- Allow all apps
- Allow specific apps and block all others
- Cake specific apps and permit all others
- Block all apps
-
If you selected Allow specific apps and block others, add the apps that you want to permit:
- Select Permit apps.
- Search for the apps that y'all desire to permit, and and so click Add together. The search results are filtered to the app publisher (Microsoft apps, Third-party apps, or Custom apps).
- When yous've called the list of apps, click Allow.
-
Similarly, if yous selected Block specific apps and permit all others, search for and add together the apps that you want to block, and then select Block.
-
Select Save.
Edit an app permission policy
You can utilize the Teams admin center to edit a policy, including the global policy and custom policies that you create.
- In the left pane of the Microsoft Teams admin middle, go to Teams apps > Permission policies.
- Select the policy by clicking to the left of the policy name, and and then select Edit.
- From here, make the changes that you want. You tin can manage settings based on the app publisher and add together and remove apps based on the permit/block setting.
- Select Salvage.
Assign a custom app permission policy to users
You can assign a policy direct to users, either individually or at calibration through a batch assignment (if supported for the policy type), or to a group that the users are members of (if supported for the policy type).
To learn about the different ways that you can assign policies to users, meet Assign policies to your users in Teams.
Manage org-wide app settings for Microsoft 365 Government
In a Microsoft 365 Authorities - GCCH and DoD deployment of Teams, it'due south important to know the following well-nigh 3rd-party app settings, which are unique to GCCH and DoD.
In GCC, GCCH, and DoD deployments, all tertiary-party apps are blocked past default. Additionally, in GCC, you run across the following notation about managing third-party apps on the app permission policies page in the Microsoft Teams admin center.

Note
In GCCH and DOD clouds, the 3rd-party apps are non available.
Use org-broad app settings to control whether users can install third-party apps. Org-wide app settings govern the behavior for all users and override whatever other app permission policies assigned to users. You tin utilize them to control malicious or problematic apps.
-
On the Permission policies page, select Org-wide app settings. Yous can and so configure the settings y'all desire in the console.
-
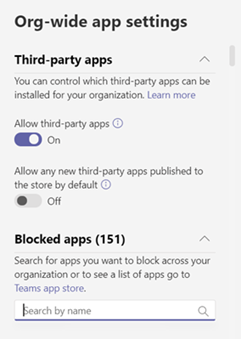
Under Third-party apps, plough off or turn on these settings to control access to tertiary-political party apps:
- Let tertiary-party apps: This controls whether users can use third-political party apps. If you plow off this setting, your users won't be able to install or use any 3rd-party apps. In a Microsoft 365 Government - GCCH and DoD deployment of Teams, this setting is off by default.
- Allow any new third-party apps published to the store past default: This controls whether new third-party apps that are published to the Teams app store become automatically available in Teams. You can only set this option if you allow third-party apps.
-
Nether Blocked apps, add the apps you lot want to block across your organization. In a Microsoft 365 Government - GCCH and DoD deployment of Teams, all 3rd-party apps are added to this listing past default. For whatever tertiary-party app y'all want to allow in your organization, remove the app from this blocked apps list. When y'all block an app org-wide, the app is automatically blocked for all your users, regardless of whether it'south allowed in any app permission policies
-
Select Save for org-wide app settings to take effect.
As mentioned earlier, to permit third-party apps, you can either edit and use the global (Org-wide default) policy or create and assign custom policies.
FAQ
Working with app permission policies
What app interactions do permission policies affect?
Permission policies govern app usage by decision-making installation, discovery, and interaction for terminate users. Admins tin still manage apps in the Microsoft Teams admin centre regardless of the permission policies assigned to them.
Can I command line of business (LOB) apps?
Yes, you tin can use app permission policies to command the rollout and distribution of custom (LOB) apps. Yous can create a custom policy or edit the global policy to allow or block custom apps based on the needs of your organization.
How exercise app permission policies relate to pinned apps and app setup policies?
You can use app setup policies together with app permission policies. Pre-pinned apps are selected from the set of enabled apps for a user. Additionally, if a user has an app permission policy that blocks an app in their app setup policy, that app won't appear in Teams.
Can I use app permission policies to restrict uploading custom apps?
You can utilize org-wide settings on the Manage apps page, or app setup policies to restrict uploading custom apps for your organisation.
To restrict specific users from uploading custom apps, use custom app policies. To acquire more, see Manage custom app policies and settings in Teams.
Does blocking an app use to Teams mobile clients?
Yes, when you cake an app, that app is blocked across all Teams clients.
User feel
What does a user experience when an app is blocked?
Users can't interact with a blocked app or its capabilities, such bots, tabs, and messaging extensions. In a shared context, such equally a team or group chat, bots can all the same ship messages to all participants of that context. Teams indicates to the user when an app is blocked.
For case, when an app is blocked, users tin't practise any of the post-obit:
- Add the app personally or to a chat or team
- Send messages to the app's bot
- Perform push button deportment that send information dorsum to the app, such equally actionable messages
- View the app's tab
- Prepare connectors to receive notifications
- Use the app's messaging extension
The legacy portal allowed controlling apps at the organization level, which means when an app is blocked, information technology's blocked for all users in the organization. Blocking an app on the Manage apps folio works exactly the aforementioned style.
For app permission policies assigned to specific users, if an app with bot or connector adequacy was allowed and and so blocked, and if the app is then immune only for some users in a shared context, members of a grouping chat or channel that don't take permission to that app can meet the message history and messages that were posted past the bot or connector, but tin't interact with it.
Admin settings for apps in Teams
Assign policies to your users in Teams
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/microsoftteams/teams-app-permission-policies
0 Response to "Teamapp File Type Not Accepted"
Post a Comment